Recent Posts
- Simple Serial I2c Programmer
- Jetix Pucca Race Game
- After School Programs In Oakland Ca
- Nuke Tutorials Rapidshare Free
- Debian Install German Locales
- Template Html Restaurant
- Activar Windows 7 Ultimate Loader Extreme Edition
- Iseki Hydraulic Manual Log
- How To Get A Boiler License In Wisconsin Channel
- Digital Satellite Tv Tuner Driver Software
- Windows 7 Loader How To Uninstall Other Cracks Windows
- Swiss Manager Pro
- Garageband Instrument Downloads
- Download Crack Uefa Champions League 2005 Ps2
- Office 2013 Crack Keygen Activator
Crack Wpa Tkip Windows
Crack Wpa Tkip Windows' title='Crack Wpa Tkip Windows' /> Aircrack ngDescription. Airodump ng is used for packet capturing of raw 8. WEP IVs Initialization Vector for the intent of using them with aircrack ng. If you have a GPS receiver connected to the computer, airodump ng is capable of logging the coordinates of the found access points. Additionally, airodump ng writes out several files containing the details of all access points and clients seen. Before running airodump ng, you may start the airmon ng script to list the detected wireless interfaces. It is possible, but not recommended, to run Kismet and airodump ng at the same time. Save only captured IVs. Use GPSd. write lt prefix Dump file prefix. Record all beacons in dump file. Display update delay in seconds. Prints ackctsrts statistics. Hides known stations for showack. Description. Aircrackng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security Monitoring Packet capture and. EthicalHacking/wireless1.png' alt='Crack Wpa Tkip Windows' title='Crack Wpa Tkip Windows' />
Aircrack ngDescription. Airodump ng is used for packet capturing of raw 8. WEP IVs Initialization Vector for the intent of using them with aircrack ng. If you have a GPS receiver connected to the computer, airodump ng is capable of logging the coordinates of the found access points. Additionally, airodump ng writes out several files containing the details of all access points and clients seen. Before running airodump ng, you may start the airmon ng script to list the detected wireless interfaces. It is possible, but not recommended, to run Kismet and airodump ng at the same time. Save only captured IVs. Use GPSd. write lt prefix Dump file prefix. Record all beacons in dump file. Display update delay in seconds. Prints ackctsrts statistics. Hides known stations for showack. Description. Aircrackng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security Monitoring Packet capture and. EthicalHacking/wireless1.png' alt='Crack Wpa Tkip Windows' title='Crack Wpa Tkip Windows' />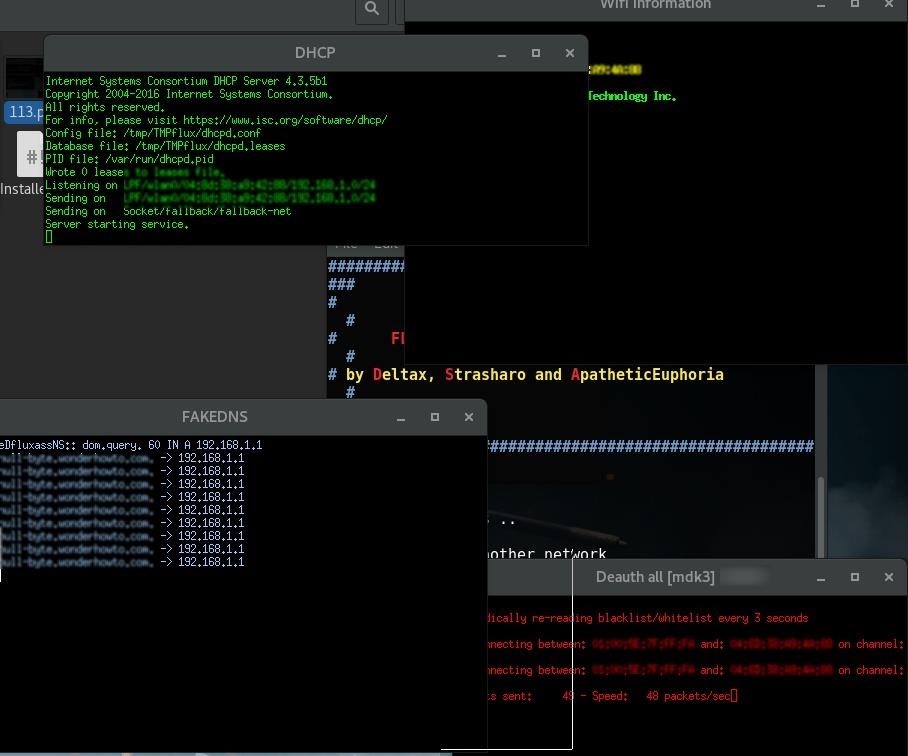 Security researchers say theyve developed a way to partially crack the WiFi Protected Access WPA encryption standard used to protect data on many. WPA2 WiFi Protected Access 2 is a network security technology commonly used on WiFi wireless networks. Its an upgrade from the original WPA technology, which was. Today we will learn about 5 Steps Wifi Hacking Cracking WPA2 Password. A lot of readers send many request regarding how to crack wireless WPA2 password in our. WEP, WPA, and WPA2 are standards for wireless networking. Which is best for a home network WEP is the older standard and is widely used. However, it can. Time in ms between hopping channels. Time before removing the APclient. Default 1. 20 seconds. Read packets from that file. Active Scanning Simulation. Display manufacturer from IEEE OUI list. Display AP Uptime from Beacon Timestamp. Display WPS information if any. Output format. Possible values. Short format o. The option can be specified multiple times. In this case, each file format. Only ivs or pcap can be used, not both. Removes the message that says. Output files write interval in seconds. Filter options. encrypt lt suite Filter APs by cipher suite. Filter APs by mask. Filter APs by BSSID. Filter APs by ESSID. Filter APs by ESSID using a regular. Filter unassociated clients. By default, airodump ng hop on 2. GHz channels. You can make it capture on otherspecific channels by using. Capture on specific channels. Band on which airodump ng should hop. C lt frequencies Uses these frequencies in MHz to hop. Set channel switching method. FIFO default. 1 Round Robin. Hop on last. s same as cswitch. Displays this usage screen. You can convert. Usage Tips. Whats the meaning of the fields displayed by airodump ng Heres an example screenshot. CH 9 Elapsed 1 min 2. Alternative15.png' alt='Crack Wpa Tkip Windows' title='Crack Wpa Tkip Windows' />WPA handshake 0. C 7. E 4. 0 8. BSSID PWR RXQ Beacons Data, s CH MB ENC CIPHER AUTH ESSID. B 1. C AA 1. D 1. Start studying Security. Learn vocabulary, terms, and more with flashcards, games, and other study tools. Aircrackng is a network software suite consisting of a detector, packet sniffer, WEP and WPAWPA2PSK cracker and analysis tool for 802. LANs. OPN NETGEAR. C 7. A 4. 1 8. WEP WEP bigbear. C 7. E 4. 0 8. WPA TKIP PSK teddy. BSSID STATION PWR Rate Lost Packets Probes. C 7. A 4. 1 8. F B5 3. A4 3. F 8. D 1. C 7. A 4. 1 8. C 4. 1 5. D1 D1 1 3. C 7. E 4. F B5 FD FB C2 3. The first line shows the current channel, elapsed running time, current date and optionally if a WPAWPA2 handshake was detected. In the example above, WPA handshake 0. C 7. E 4. 0 8. WPAWPA2 handshake was successfully captured for the BSSID. In the example above the client rate of 3. The first number is the last data rate from the AP BSSID to the Client STATION. Hp Multimedia Card Reader Driver Windows 7. In this case 3. 6 megabits per second. The second number is the last data rate from Client STATION to the AP BSSID. In this case 2. 4 megabits per second. These rates may potentially change on each packet transmission. It is simply the last speed seen. These rates are only displayed when locked to a single channel, the APclient transmission speeds are displayed as part of the clients listed at the bottom. NOTE APs need more then one packet to appear on the screen. APs with a single packet are not displayed. Field. Description. BSSIDMAC address of the access point. In the Client section, a BSSID of not associated means that the client is not associated with any AP. In this unassociated state, it is searching for an AP to connect with. PWRSignal level reported by the card. Its signification depends on the driver, but as the signal gets higher you get closer to the AP or the station. If the BSSID PWR is 1, then the driver doesnt support signal level reporting. If the PWR is 1 for a limited number of stations then this is for a packet which came from the AP to the client but the client transmissions are out of range for your card. Meaning you are hearing only 12 of the communication. If all clients have PWR as 1 then the driver doesnt support signal level reporting. RXQReceive Quality as measured by the percentage of packets management and data frames successfully received over the last 1. See note below for a more detailed explanation. Beacons. Number of announcements packets sent by the AP. Each access point sends about ten beacons per second at the lowest rate 1. M, so they can usually be picked up from very far. Data. Number of captured data packets if WEP, unique IV count, including data broadcast packets. Number of data packets per second measure over the last 1. CHChannel number taken from beacon packets. Note sometimes packets from other channels are captured even if airodump ng is not hopping, because of radio interference. MBMaximum speed supported by the AP. If MB 1. 1, its 8. MB 2. 2 its 8. The dot after 5. Displays e following the MB speed value if the network has Qo. S enabled. ENCEncryption algorithm in use. OPN no encryption,WEP WEP or higher not enough data to choose between WEP and WPAWPA2, WEP without the question mark indicates static or dynamic WEP, and WPA or WPA2 if TKIP or CCMP is present. CIPHERThe cipher detected. One of CCMP, WRAP, TKIP, WEP, WEP4. WEP1. 04. Not mandatory, but TKIP is typically used with WPA and CCMP is typically used with WPA2. WEP4. 0 is displayed when the key index is greater then 0. The standard states that the index can be 0 3 for 4. AUTHThe authentication protocol used. One of MGT WPAWPA2 using a separate authentication server, SKA shared key for WEP, PSK pre shared key for WPAWPA2, or OPN open for WEP. ESSIDShows the wireless network name. The so called SSID, which can be empty if SSID hiding is activated. In this case, airodump ng will try to recover the SSID from probe responses and association requests. See this section for more information concerning hidden ESSIDs. STATIONMAC address of each associated station or stations searching for an AP to connect with. Clients not currently associated with an AP have a BSSID of not associated. Lost. The number of data packets lost over the last 1. See note below for a more detailed explanation. Packets. The number of data packets sent by the client. Probes. The ESSIDs probed by the client. These are the networks the client is trying to connect to if it is not currently connected. RXQ expanded Its measured over all management and data frames. The received frames contain a sequence number which is added by the sending access point. RXQ 1. 00 means that all packets were received from the access point in numerical sequence and none were missing. Thats the clue, this allows you to read more things out of this value. Lets say you got 1. RXQ and all 1. 0 or whatever the rate beacons per second coming in. Now all of a sudden the RXQ drops below 9. Thus you know that the AP is sending frames to a client but you cant hear the client nor the AP sending to the client need to get closer. Another thing would be, that you got a 1. MB card to monitor and capture frames say a prism. AP. The AP is set to 5. MBit and then again the RXQ drops, so you know that there is at least one 5. MBit client connected to the AP. N. B. RXQ column will only be shown if you are locked on a single channel, not channel hopping. Lost expanded It means lost packets coming from the client.
Security researchers say theyve developed a way to partially crack the WiFi Protected Access WPA encryption standard used to protect data on many. WPA2 WiFi Protected Access 2 is a network security technology commonly used on WiFi wireless networks. Its an upgrade from the original WPA technology, which was. Today we will learn about 5 Steps Wifi Hacking Cracking WPA2 Password. A lot of readers send many request regarding how to crack wireless WPA2 password in our. WEP, WPA, and WPA2 are standards for wireless networking. Which is best for a home network WEP is the older standard and is widely used. However, it can. Time in ms between hopping channels. Time before removing the APclient. Default 1. 20 seconds. Read packets from that file. Active Scanning Simulation. Display manufacturer from IEEE OUI list. Display AP Uptime from Beacon Timestamp. Display WPS information if any. Output format. Possible values. Short format o. The option can be specified multiple times. In this case, each file format. Only ivs or pcap can be used, not both. Removes the message that says. Output files write interval in seconds. Filter options. encrypt lt suite Filter APs by cipher suite. Filter APs by mask. Filter APs by BSSID. Filter APs by ESSID. Filter APs by ESSID using a regular. Filter unassociated clients. By default, airodump ng hop on 2. GHz channels. You can make it capture on otherspecific channels by using. Capture on specific channels. Band on which airodump ng should hop. C lt frequencies Uses these frequencies in MHz to hop. Set channel switching method. FIFO default. 1 Round Robin. Hop on last. s same as cswitch. Displays this usage screen. You can convert. Usage Tips. Whats the meaning of the fields displayed by airodump ng Heres an example screenshot. CH 9 Elapsed 1 min 2. Alternative15.png' alt='Crack Wpa Tkip Windows' title='Crack Wpa Tkip Windows' />WPA handshake 0. C 7. E 4. 0 8. BSSID PWR RXQ Beacons Data, s CH MB ENC CIPHER AUTH ESSID. B 1. C AA 1. D 1. Start studying Security. Learn vocabulary, terms, and more with flashcards, games, and other study tools. Aircrackng is a network software suite consisting of a detector, packet sniffer, WEP and WPAWPA2PSK cracker and analysis tool for 802. LANs. OPN NETGEAR. C 7. A 4. 1 8. WEP WEP bigbear. C 7. E 4. 0 8. WPA TKIP PSK teddy. BSSID STATION PWR Rate Lost Packets Probes. C 7. A 4. 1 8. F B5 3. A4 3. F 8. D 1. C 7. A 4. 1 8. C 4. 1 5. D1 D1 1 3. C 7. E 4. F B5 FD FB C2 3. The first line shows the current channel, elapsed running time, current date and optionally if a WPAWPA2 handshake was detected. In the example above, WPA handshake 0. C 7. E 4. 0 8. WPAWPA2 handshake was successfully captured for the BSSID. In the example above the client rate of 3. The first number is the last data rate from the AP BSSID to the Client STATION. Hp Multimedia Card Reader Driver Windows 7. In this case 3. 6 megabits per second. The second number is the last data rate from Client STATION to the AP BSSID. In this case 2. 4 megabits per second. These rates may potentially change on each packet transmission. It is simply the last speed seen. These rates are only displayed when locked to a single channel, the APclient transmission speeds are displayed as part of the clients listed at the bottom. NOTE APs need more then one packet to appear on the screen. APs with a single packet are not displayed. Field. Description. BSSIDMAC address of the access point. In the Client section, a BSSID of not associated means that the client is not associated with any AP. In this unassociated state, it is searching for an AP to connect with. PWRSignal level reported by the card. Its signification depends on the driver, but as the signal gets higher you get closer to the AP or the station. If the BSSID PWR is 1, then the driver doesnt support signal level reporting. If the PWR is 1 for a limited number of stations then this is for a packet which came from the AP to the client but the client transmissions are out of range for your card. Meaning you are hearing only 12 of the communication. If all clients have PWR as 1 then the driver doesnt support signal level reporting. RXQReceive Quality as measured by the percentage of packets management and data frames successfully received over the last 1. See note below for a more detailed explanation. Beacons. Number of announcements packets sent by the AP. Each access point sends about ten beacons per second at the lowest rate 1. M, so they can usually be picked up from very far. Data. Number of captured data packets if WEP, unique IV count, including data broadcast packets. Number of data packets per second measure over the last 1. CHChannel number taken from beacon packets. Note sometimes packets from other channels are captured even if airodump ng is not hopping, because of radio interference. MBMaximum speed supported by the AP. If MB 1. 1, its 8. MB 2. 2 its 8. The dot after 5. Displays e following the MB speed value if the network has Qo. S enabled. ENCEncryption algorithm in use. OPN no encryption,WEP WEP or higher not enough data to choose between WEP and WPAWPA2, WEP without the question mark indicates static or dynamic WEP, and WPA or WPA2 if TKIP or CCMP is present. CIPHERThe cipher detected. One of CCMP, WRAP, TKIP, WEP, WEP4. WEP1. 04. Not mandatory, but TKIP is typically used with WPA and CCMP is typically used with WPA2. WEP4. 0 is displayed when the key index is greater then 0. The standard states that the index can be 0 3 for 4. AUTHThe authentication protocol used. One of MGT WPAWPA2 using a separate authentication server, SKA shared key for WEP, PSK pre shared key for WPAWPA2, or OPN open for WEP. ESSIDShows the wireless network name. The so called SSID, which can be empty if SSID hiding is activated. In this case, airodump ng will try to recover the SSID from probe responses and association requests. See this section for more information concerning hidden ESSIDs. STATIONMAC address of each associated station or stations searching for an AP to connect with. Clients not currently associated with an AP have a BSSID of not associated. Lost. The number of data packets lost over the last 1. See note below for a more detailed explanation. Packets. The number of data packets sent by the client. Probes. The ESSIDs probed by the client. These are the networks the client is trying to connect to if it is not currently connected. RXQ expanded Its measured over all management and data frames. The received frames contain a sequence number which is added by the sending access point. RXQ 1. 00 means that all packets were received from the access point in numerical sequence and none were missing. Thats the clue, this allows you to read more things out of this value. Lets say you got 1. RXQ and all 1. 0 or whatever the rate beacons per second coming in. Now all of a sudden the RXQ drops below 9. Thus you know that the AP is sending frames to a client but you cant hear the client nor the AP sending to the client need to get closer. Another thing would be, that you got a 1. MB card to monitor and capture frames say a prism. AP. The AP is set to 5. MBit and then again the RXQ drops, so you know that there is at least one 5. MBit client connected to the AP. N. B. RXQ column will only be shown if you are locked on a single channel, not channel hopping. Lost expanded It means lost packets coming from the client.